The information below includes a description of the vulnerability and details steps recommended by Infineon and Fujitsu that users should take to secure affected product lines.
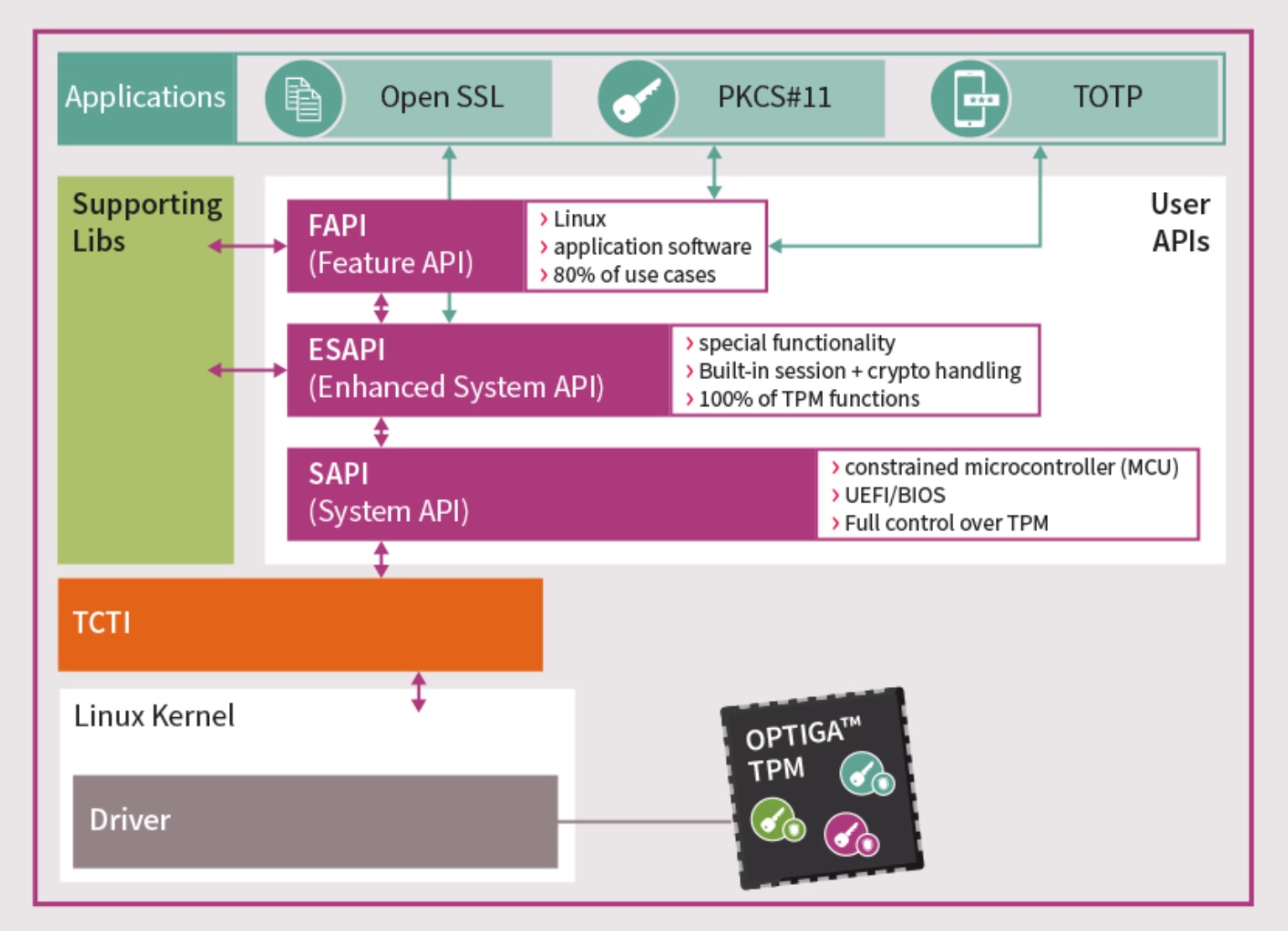
OPTIGA TPM SLM 9670 The Infineon OPTIGA TPM SLM 9670 is a fully TCG standard compliant TPM 2.0 with a SPI interface. It addresses the requirements of industrial and other demanding applications where an extended temperature range, an extended lifetime and industrial-grade quality are key. A system health check supported by Infineon’s OPTIGA TM TPM lets users check that their devices have not been manipulated. The TPM provides a secured identity and storage space for system control mechanisms that may check whether hardware and software are still running as intended. Upgrading the Firmware on Infineon TPM's. In early October of 2017, researchers announced, publicly, a cryptographic vulnerability in the RSA generation algorithms found within practically every TPM, using Infineon's RSA library. This vulnerability would effectively allow an attacker to easily guess the private key component of the RSA key.
At the 'Infineon TPM Professional Package Ver. 4.3.3137.0 ' screen, click 'Next'. At the 'License Agreement' dialog, read the agreement, then, if you agree, click 'I Agree' to continue with the installation. At the 'Browse For Folder' screen, select the destination where you would like to save the extracted file. HPSBHF03568 rev. 11 - Infineon TPM Security Update VULNERABILITY SUMMARY A security vulnerability was identified in the RSA key generation method used by TPM products listed below. This leaves the keys potentially vulnerable via targeted, computationally expensive attacks.
Summary:
Infineon Tpm Firmware Update
A vulnerability in Infineon TPM hardware has been discovered recently with outdated TPM firmware using an algorithm that generates weaker RSA keys. This page provides information on how to update outdated TPM firmware.
For more detailed information please refer to the Infineon web site:
http://www.infineon.com/TPM-update
Microsoft has published additional information relating to operating systems. For detailed information please refer to the Microsoft web site: https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/ADV170012
Affected Products:
An overview of the Fujitsu affected products can be found here:
| Model Name | Original | Updated | Update Type | Release Date |
|---|---|---|---|---|
| LIFEBOOK E544 LIFEBOOK E554 | FW4.32 | FW4.34 | FW Update Utility | Feb. 2018 |
| LIFEBOOK E546 LIFEBOOK E556 (come with TPM1.2) | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| LIFEBOOK E546 LIFEBOOK E556 (come with TPM2.0) | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK E547 LIFEBOOK E557 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK E734 LIFEBOOK E744 LIFEBOOK E754 | FW4.32 | FW4.34 | FW Update Utility | Feb. 2018 |
| LIFEBOOK E736 LIFEBOOK E746 LIFEBOOK E756 (come with TPM1.2) | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| LIFEBOOK E736 LIFEBOOK E746 LIFEBOOK E756 (come with TPM2.0) | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK P727 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK S904 | FW4.32 | FW4.34 | FW Update Utility | Feb. 2018 |
| LIFEBOOK S935 | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| LIFEBOOK S936 (come with TPM1.2) | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| LIFEBOOK S936 (come with TPM2.0) | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK S937 | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK T725 | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| LIFEBOOK T726 | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK T734 | FW4.32 | FW4.34 | FW Update Utility | Feb. 2018 |
| LIFEBOOK T904 | FW4.32 | FW4.34 | FW Update Utility | Feb. 2018 |
| LIFEBOOK T935 | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| LIFEBOOK T936 | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK T937 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK U536 (come with TPM1.2) | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| LIFEBOOK U536 (come with TPM2.0) | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK U537 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK UH554 LIFEBOOK UH574 | FW4.32 | FW4.34 | FW Update Utility | Feb. 2018 |
| LIFEBOOK U727 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK U745 | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK U747 LIFEBOOK U757 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| LIFEBOOK U937 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| Model Name | Original | Updated | Update Type | Release Date |
|---|---|---|---|---|
| STYLISTIC Q616 | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| STYLISTIC Q665 | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| STYLISTIC Q704 | FW4.32 | FW4.34 | FW Update Utility | Feb. 2018 |
| STYLISTIC Q736 | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| STYLISTIC Q737 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| STYLISTIC Q775 | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| STYLISTIC R726 (come with TPM1.2) | FW4.40 | FW4.43 | FW Update Utility | Available for W7 & W10, W8.1 Dec 2017 |
| STYLISTIC R726 (come with TPM2.0) | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| Model Name | Original | Updated | Update Type | Release Date |
|---|---|---|---|---|
| CELSIUS H730 | FW4.32 | FW4.34 | FW Update Utility | Feb. 2018 |
| CELSIUS H760 | FW5.51 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| CELSIUS H770 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
| CELSIUS H970 | FW5.61 | FW5.62 | BIOS update and FW Tool*2 | Jan. 2018 |
*1: Dates are subject to change
*2: The FW Tool must be used with BIOS update, although the BIOS update can be applied separately.
| CELSIUS (WorkStation) | Please refer to the following site. http://support.ts.fujitsu.com/content/intel_firmware_SA86.asp |
|---|---|
| ESPRIMO (Desktop) | |
| FUTRO (Thin Client) |
Fujitsu is providing an easy to use Windows-based tool for end customers to identify whether a TPM is installed in their system. If the tool finds a TPM in the system, then it will show the relevant TPM and firmware version. This tool can be found here: TPM Information Tool
Please note: for some affected products, TPM was sold as an optional component. This means that not all systems are affected by this issue.
Recommended steps:
- Consult the list of affected Fujitsu systems.
- Before updating the TPM firmware, please make sure that you save your encryption keys, decrypt all your encrypted data and backup to an external storage device, to avoid any data loss.
For Notebook or Tablet to download the respective TPM firmware update package for your system, please go to the Fujitsu support page and perform the following steps:
1. Select “Product Type”.
2. Select “Series”.
3. Select “Model”.
4. Select “OS”.
5. Download and install the latest BIOS or TPM firmware update package from the “BIOS“ section.
For Desktop and Workstation and ThinClient, please go to Fujitsu support page and follow the instructions.
For inquiries related to this issue, please contact the following dedicated hotline:WARNING: Clearing the TPM resets it to factory defaults. All created keys will be deleted and you will therefore lose access to any data encrypted by those keys.
For more detailed information regarding TPM Clear please refer also to the following Microsoft site:
https://docs.microsoft.com/en-us/windows/device-security/tpm/initialize-and-configure-ownership-of-the-tpm#clear-all-the-keys-from-the-tpm
In early October of 2017, researchers announced, publicly, a cryptographic vulnerability in the RSA generation algorithms found within practically every TPM, using Infineon's RSA library. This vulnerability would effectively allow an attacker to easily guess the private key component of the RSA key stored within the TPM - rendering the protections and insurances granted by the TPM useless. Turns out, many TPM's actually use Infineon's technologies, meaning many TPM's are vulnerability - including all Asus and Gigabyte TPM's (that I know of).
tl;dr - TPM broke, I sad, TPM need fix.

Since the point of TPM's is to perform key protection inside hardware, a software fix is impossible. This is so difficult to mitigate that Window's just resorts to emitting a warning in the Event Logs like the one below:
Now, 6 months later and over a year since Infineon was notified of this issue, Asus and Gigabyte have yet to release updates for their TPM's. Although, I'm not particularly surprised considering most consumers would likely brick their machine's when trying to update (or not need to update to begin with). Thankfully, many enterprise-centered company's use these Infineon based TPM's, meaning we, the consumers, can piggyback off of enterprise clients shouting for a fix.
In this case, it turns out that the Asus and Gigabyte TPM's are effectively the same one's found in some Supermicro servers, and of course, Supermicro had to release firmware updates - updates that we can use.

Infineon Tpm Firmware Update
Getting Started
Before I get started, I want to make sure the TPM is working in my device. I can ask Window's about it via the Get-TPM command.
Getting the Firmware
Everything looks good! Now to get the firmware. I found a compatible version on Supermicro's driver site (Driver FTP).
Infineon Tpm Software
Looking through the files extracted files, there are two directories:
The important files are these:
I'm going to copy the above to the same folder, because I'm lazy.
Now .workspace contains the following files:
Now to upgrading the firmware!
Upgrading the Firmware
Let's make sure TPMFactoryUpd.exe detects the TPM.
And it does, sweet! Now to run the upgrade.
Sad panda, it turns out we need to disable the TPM module in the BIOS/UEFI before we can flash the firmware update. Time to connect my Spider KVM and boot into the UEFI menu. BTW, Spiders are awesome, but don't pay full price!
Now to disable the TPM.
After booting back into Windows, it looks like disabling the TPM fixes the Empty Buffer problem:
Now I can try to update the TPM again.
And it works!
Wrapping Things Up
A disabled TPM is rather useless, time to boot back into the UEFI menus to enable it.
And since this vulnerability is for RSA key generation, it's best to reset all generated keys. I used a TPM clear to do this, plus a reboot.
After getting back into Windows, I'm greeted with a lovely success message.
And as a final check, it looks like the ManufacturerVersion was updated to 5.62.
Yeah, no more weak keys!